
Medigate, Armis, Zingbox, ORDR ? Why Choose IoTSecure Instead!
Medigate, Armis, Zingbox, ORDR and other vendors, including IoTSecure, can all help to discover and secure IoT devices.
But, what do these solutions do? How do they work? And, how do they differ?
Maybe you have already researched unmanaged medical and IoT device security risks. And you may have come across expert publications on the topic from the likes of FDA or NIST.
Or, you read about IoT Security from other industry analysts such as EY, Deloitte, PwC , Travelers or Gartner.
Perhaps you checked out the Top 10 IoT Threats research from OWASP or one of our own blogs on Medical / IoT security vulnerabilities.
Let’s say you are warming up to Gartner’s recommendation that real-time discovery, visibility and control are critical to address IoT security
Now, you may want to sort out the IoT security market and determine which vendors to talk with.
Let’s see how they compare.
Core Capabilities of IoT Security Solutions
IoTSecure and other IoT security solutions like Medigate, Armis, Zingbox or ORDR all provide greater device visibility and threat detection. And, they can leverage that new level of information in with existing tools. In general, they provide:
Device Visibility
- Discover and Identify devices by make and model number to know what is on the network and where it is on the network.
- Device Communications, both internal and external communications
Passive Threat Detection
- Device-Level, Passive Monitoring to detect suspicious, malicious and anomalous device behavior
- CVE/CERT Mapping that alerts when device is on the network that has come under a security advisory
Integration and Control
- Integrating device identification detail into solutions such as NAC, SIEM, Asset Inventory, Help Desk solutions, Firewalls, etc. This is to support automated asset inventory and network access, network segmentation, mitigation and remediation decisions that leverage existing tools and workflows.
Core Technology Differences
As with any solution such as Medigate , Armis , Zingbox , ORDR or others, vendors will each have feature differences. And, vendors may add new features at different rates. To that end, feature focus is not the focus here. For this discussion, we are focused on core technology differences and what IoTSecure does that is unique and better vs. most other vendors.
First, a quick summary comparison, followed by a more detailed discussion.
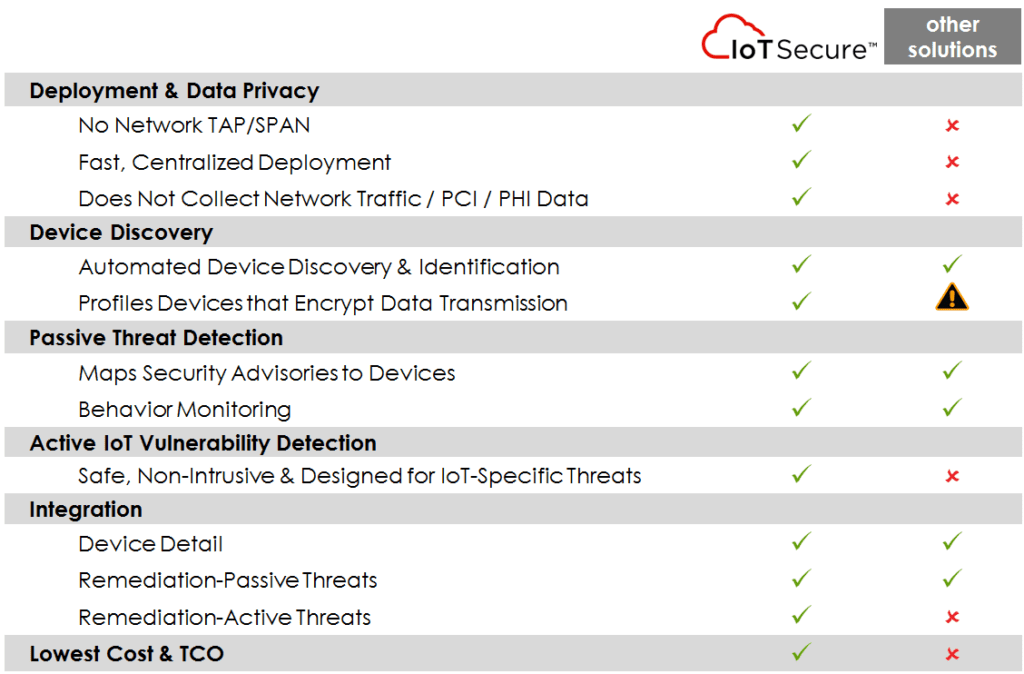
Deployment & Data Privacy Differences
Most competitive solutions such as Medigate, Armis, Zingbox and ORDR commonly deploy with network TAP/SPAN Ports to collect needed data.
Common deployment Using Network TAP/SPAN Ports
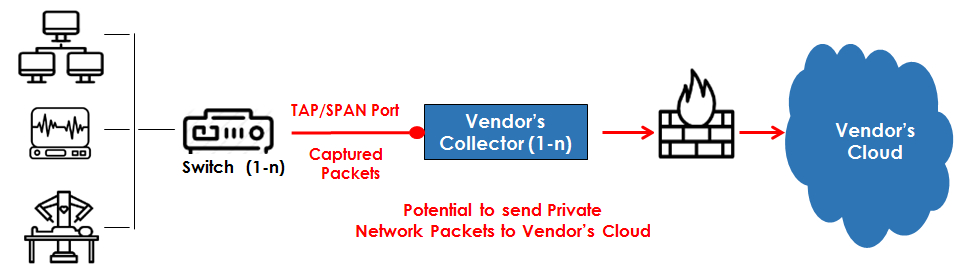
Cons with Network TAP/SPAN port deployments
Increased Data Privacy Risks
With network TAP/SPAN Ports, vendors collect private, sensitive network packets / PHI into their solution. Vendors can claim that they filter out private/sensitive data and only send metadata to their cloud for analysis. The question is: Do you trust the vendor to do that and do it 100% of the time?
Increased Expense, Deployment and Maintenance
Network TAPS can be expensive, and even more so in larger environments. This can involve locating and configuring all the switches needed to ensure that all traffic is being captured from all devices. Then, data collectors will need to be bought, installed and maintained for each TAP. This can be a massive undertaking. As an option, you could also spend extra money to license and maintain a traffic aggregator solution to feed the data into the vendor’s solution. Perhaps less work, but expensive nonetheless.
Increased Switch Load & Network Performance Risks
The risk here is that the switch can become taxed with duplicating the packets to send to the vendor’s solution. This can cause network performance issues.
Limited Discovery & Device Identification
Since competitive systems rely on actual network traffic for data, they can only see devices where the network has been tapped. So, you’ll need on-going planning and work to ensure that traffic from all devices is being captured. Devices that encrypt data transmission can also represent a limiting factor to device visibility and profiling. Also, SPAN ports are known to drops packets on oversubscribed ports. They can also be easily misconfigured / turned off which can further limit device profiling.
Why IoTSecure?
No Network TAP/SPAN Deployment
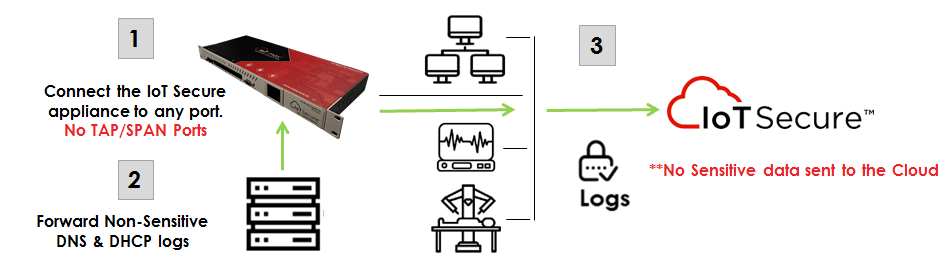
The IoTSecure solution does not use network TAP/SPAN ports. A PoC deploys in a few minutes using a single IoT Security appliance.
Additionally, a single appliance is all that is needed for most enterprises.
The deployment is simple:
1. Connect the IoT Security Appliance anywhere on the network. It only collects non-sensitive data to profile devices. Get results in 72 hours or less. This is all that is needed to conduct a proof-of-concept deployment.
2. For a full deployment, simply provide DNS and DHCP logs. These logs do not contain sensitive data and collection is commonly done in less that 1 hour.
The IoTSecure approach vs. a Network TAP/SPAN deployment delivers these benefits:
- Greatly accelerates and simplifies deployment and on-going maintenance
- Typical deployment requires only one (1) appliance per organization, regardless of the number of locations
- Reduces Costs
- Reduces Network Performance Risks
- Keeps your private data…Private!

Threat Detection Differences
Medigate, Armis, Zingbox and ORDR Provide Passive Monitoring and Security Advisory Mapping, but what about IoT vulnerability detection?
Medigate, Armis, Zingbox or ORDR and most competitive solutions focus on passive behavior monitoring and on mapping CVE/CERT advisories to devices on the network while leaving active inspection for traditional vulnerability scanners.
The problems with traditional vulnerability scanners on IoT are:
1. They are weak in detecting IoT-specific threats like default credentials, VXWorks and more. For example, default credentials are the #1 IoT threat described in the OWASP Top 10 IoT Threats
2. They are too intrusive to run on resource-constrained IoT devices. Scanning IoT devices can result in device interference or crashes. In turn, this can increase IT workload and leave devices untested.
3. Scanners are usually scheduled to run periodically and are not real-time. Since IoT devices are commonly deployed by users and departments without IT, vulnerable IoT devices can be on the network for some time before or even if IT ever knows about it. Some competitive solution can integrate with vulnerability scanners to feed them device detail, but the problems in 1 and 2 above are still present.
But, is it possible to do Active vulnerability detection without device interference and in real time?
Yes, with IoTSecure PortSafeTM Inspection!
Why IoTSecure? Enter PortSafeTM – Unique, Safe Vulnerability Detection Designed for IoT
Like competitive solutions, IoTSecure also does passive monitoring and security advisory mapping to devices on the network. But, the difference is IoTSecure PortSafeTM Inspection.
PortSafeTM provides new and unique capabilities to conduct active, but safe inspection on sensitive IoT devices. As a result, you can now do vulnerability testing on IoT , like medical devices, that would otherwise need to be excluded from intrusive vulnerability scans.
Unlike traditional vulnerability scanners that use brute force testing, IoTSecure PortSafeTM first understands what the device is and how to safely test it, before any testing occurs. With this knowledge, it can then gently test the device to detect IoT vulnerabilities precisely, intelligently and non-intrusively.
PortSafeTM Inspection – No Device Interference
To date and with millions of devices that are inspected continuously, IoTSecure has yet to receive any customer reports of ever interfering with any device…even sensitive medical devices. This includes customers like a 9,000 bed healthcare system and a 35,000 employee healthcare system which has one of the top 10 largest hospitals in the U.S.
These healthcare systems safely inspect medical devices with IoTSecure.
PortSafeTM is also configurable so that organization can customize which devices are inspected, or inspection can be disabled completely.
And, it includes unmatched default credential detection to provide coverage for the #1 IoT threat described in the OWASP IoT Top 10.
PortSafeTM provides new and unique capabilities to conduct active, but safe inspection on sensitive IoT devices. As a result, you can now do vulnerability testing on IoT , like medical devices, that would otherwise need to be excluded from intrusive vulnerability scans.

Integration & Operationalization Differences
Integrating Device Detail & Threat Data
Most IoT Security solutions, like Medigate, Armis, Zingbox and ORDR and others, including IoTSecure, provide integration capabilities. Integration capabilities feed device detail and/or threat data into systems like NAC, SIEM, Firewalls, Asset Management, IT Service Management, etc. It helps to support activities such as segmentation, device blocking and creation of automated security policy. However, the scope of mitigation commonly applies to only threats detected through behavior monitoring or security advisory mapping.
What’s Missing with Competitive Solutions?
IoT-specific vulnerabilities that are only be detected by active inspection.
Why IoTSecure?
IoTSecure creates mitigation policy for both passive, behavioral threats and Portsafe TM active inspection results
This is where IoTSecure takes it a step further, beyond protection for just behavioral threats.
IoTSecure also creates mitigation policy based on PortSafeTM Active Inspection.
1. It finds IoT-specific vulnerabilities though its active but safe vulnerability inspection that competitive systems and vulnerability scanners commonly miss.
2. It creates a compensating control to mitigate those threats – with No Downtime.
After IoTSecure identifies vulnerabilities, it can automatically create a mitigation security policy that gets passed to the NAC, firewall or switch.

Cost Differences
IoTSecure typically reduces costs by 30% or more vs. most competitive solutions.
In addition, IoTSecure further reduces the costs and administrative overhead that goes along with network TAP/SPAN port deployments and on-going maintenance.
Do You Know Your IoT Risks? Find Out in Minutes…FREE

Request Your FREE IoT-mini
![]() More Resources
More Resources
Check Out Pricing
See Pricing
Request a Demo or a FREE Assessment
Schedule a Call or Demo
Check out our IoT security products in more detail
See IoTSecure Products
Disclaimer-IoTSecure is not a representative of nor affiliated or associated with Medigate, Armis, Zingbox, ORDR or any other IoT security solution or vendor.



