How We Help
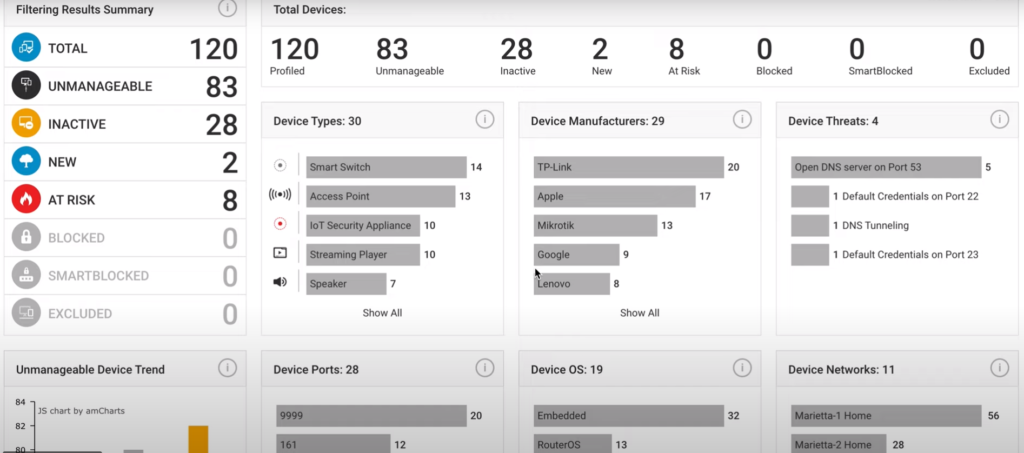
For as long as network security standards have existed, the first and most important aspect is the control and management of those assets. Because of the core nature of this tenant, the tools that do this for traditional IT endpoints, like servers and workstations, are well-made and do the job well. But, when you look at the litany of other endpoints on a modern network, like Shadow IT, IoT, OT, ICS/SCADA, BioMed, and the endless list of “smart” devices, these traditional tools do not do such a good job. Find out what is on your network, EVERYTHING, today with IoTSecure.
Most security programs are good at maintaining, monitoring, and securing their traditional endpoints (servers, Laptops, networking equipment, etc.). These more conventional devices can run software agents and be managed centrally with tools like Active Directory. However, IoT, OT, BioMed, user-connected and Shadow IT devices often don’t support endpoint agents nor produce logs. And, effective behavior monitoring of these single-purpose devices means understanding the context of where the device should/shouldn’t be going, but that can be a manual process that just doesn’t scale.
IoTSecure’s agentless solution automatically monitors devices. And, thanks to our library of millions of profiled devices and malicious URL feeds, it understands when devices are behaving maliciously or when they are communicating where they shouldn’t …just set it and forget it to get continuous monitoring without any tuning.
Safe on Devices: The IoT-miniTM uses a proprietary non-intrusive technique called PortSafeTM Inspection. Unlike vulnerability scanners, PortSafeTM will not interfere with devices as it discovers, identifies, and does vulnerability detection on devices.
Safe on the Network: Unlike competitve solutions, the IoT-miniTM does not use network TAP/SPAN ports, so there is no addition load on the switch to duplicate packets which can cause network performance issues. Also, the IoT-miniTM generates only a small fraction of traffic vs. network scans.
The Benefit: Now you can safely and confidently discover and vulnerability test sensitive and resource-constrained devices that are excluded from intrusive vulnerability scans, without concern of crashing devices or causing network performance issues.
Want to get alerts or send all device detail and threat data to your SIEM, NAC or ITSM to get better context for decision making and remediation prioritization? Want to mitigate threats with a single click? No problem, IoTSecure can do that to help you manage devices and their risks, while saving time!